Enterprise Cyber Security Solution
The solution has extended behavior analysis capability from sandbox for a single file object to the entire endpoint system’s behavior analysis, including desktop and server computers, physical or in the cloud. Besides its proactive threat hunting capability, solution also accepts log files from different sources, automatically investigates thousands of those alerted endpoint systems, delivers fast, consistent, efficient and effective threat hunting results.
Its deep forensic behavioral based analytic algorithm can detect advanced attacks without relying on signature, static patterns, or documented IOCs. It detects Malicious Network connections, Malicious emails, APTs, root kits, zombies, Hidden downloads, File-less attacks, code injections, Ransomware , reverse shell attacks, and crypto currency mining malware. It also detects misconfiguration and security posture changes.
| Anti virus Integration with existing AV | Ransomware protection in Real-Time (Free POC on Demand) |
|---|---|
| EDR – Endpoint Detection & Response | Secure Folder for Files & Folders protection from Ransomware attack’s infection |
| Firewall Logs Analytics | Real time blocking of Ransomware/ Malware attack |
| Email security – phishing attacks protection | Automatic Auditing NIST / CIS International standards |
| SOC operation Monitoring & Analysis | Cryptocurrency mining malware attacks |
| AI/ML based scrutiny of all downloaded files for malicious threats detection |
Malicious Network connection Detection for each Endpoint |
| Data protection / USB blocking | System Roll back to known good working state |
| Vulnerability Scanning / Pen Testing | Troubleshoot Applications / login problem / missing software updates / Printer |
| Asset discovery and listing | Visibility of All managed Endpoints in the IT environment |
Advanced Security Center
The Full DETECTION Stack
- Sandbox behavioral analysis
- Vulnerability scan
- Embedded AV
- IOC query
- IOD detection
- Email scan
- Ransomware unavoidable trap
- Firewale log analysis
- WMI script analysis
- Virus Total query
- Proactive threat hunting
- Forensic investigation
Instant RESPOND
- Realtime response with network isolation
- Full stack endpoint threat investigation
- Automated triage process
- 7/24 IR service by our security experts with 20+ experiences .
- Storyline representing what, why, and how
- AL/DLdriven and rule based actionable instructions.
The Most Precise IDENTIFY
- IOD to identify the potential and hidden threats at the earliest stage.
- Proactive scheduled threat hunting process to find weakness before exploited.
- Automated auditing process covering NIST800-53, 800-171, CIS and STIG.
- Visibility to each endpoint, its user and behavioural.
- Monitoring all network connections to identify intrusion and suspicious activities.
- Identifyingmis configuration and mis behavioural when it happens.
The Most Efficient RECOVER
- Sandbox behavioral analysis
- Vulnerability scan
- Embedded AV
- IOC query
- IOD detection
- Email scan
- Ransomware unavoidable trap
- Firewail log analysis
- WMI script analysis
- Virus Total query
- Proactive threat hunting
- Forensic investigation
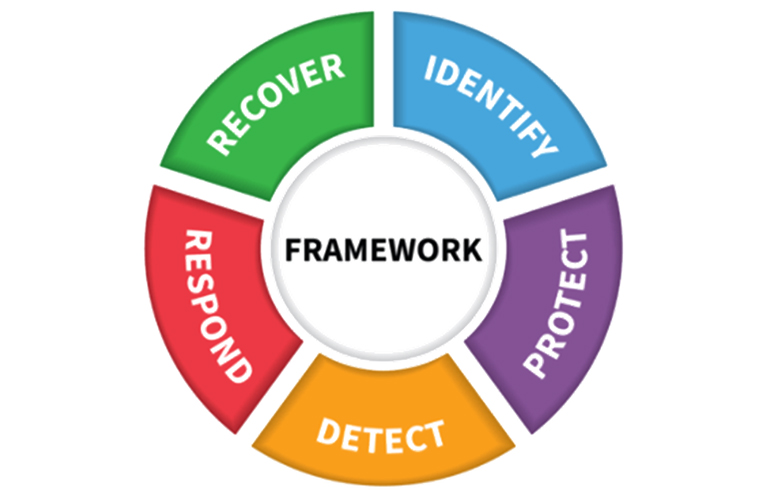
The Most completed PROTECTION
- Real time protection against malicious process, code injection memory only evasion.
- Real time protection against network intrusion passed gateway security defences.
- Fully covered protection around the system against all unknown.
- Full protection against threat coming from USB moveable devices .
- Extra protection for local user data files against ransomware attacks .
- Patent pending unavailable ransomware trap provides unbreakable protection for user data.
Holistic Cyber Security Solution
• Security Operations
• FW/IPS Logs
• EDR & Splunk Events
• Better EDR
• MDR

Feeds back into Security
Operations Workflow for threat
scoping and IT Operations
OUTPUT
Investigation Results:
• Confirmed Verdict
• IOC’s
• TTP’s / Behaviors
• Remediation Actions
• Security Posture
• Measurement
Secure and Simpler Authentication
Replace passwords with Biometric FIDO2 security Token
Maps people to unique Biometric identifiers
to Authenticate
Is aligned with FIDO U2F and FIDO2 standards.
Supports OATH-HOTP/TOTP authentication
standards.
Has an open, scalable, and interoperable
approach.
Provides a biometric 360° touch sensor that is
private by design.

Authenticate Seamlessly
• Single Token for hundreds of services
• Passwordless login to Windows Hello
• Authentication in <750 milliseconds
• Covers up to 30 FIDO2 applications

We G-Info Technology Solutions Pvt. Ltd. is a trusted name as a Cyber Security Consultant in Delhi. As a cybersecurity consultant is accountable for identifying problems, assessing security issues, assessing risk, and implementing solutions to address threats to a company’s computer networks and computer systems. Also, we can evaluate security systems and make layers of protection in a rapidly changing technology environment.
By hiring us you can get all the relevant tests and the organization’s cybersecurity measures, also we can design and implement a better defense. These consultants are sometimes known by different names, Figure out the best way to defend devices, networks, software, data, and complete information systems against possible intrusion and cyber-attacks.
As a well-known name for Cyber Security Solution Providers in India we Interview staff and department heads to determine specific security concerns and issues Also perform vulnerability testing much like a white hat hacker does, comprising risk analyses and security assessments
We can research current security standards and systems and the latest verification protocols with the use of our vast knowledge and years of experience to advise.
